risks and threats
-
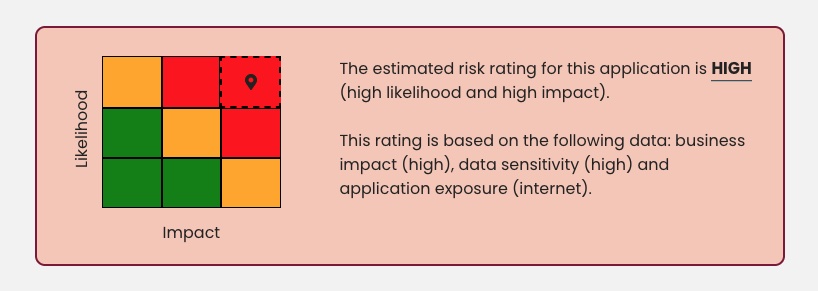
Application Risk is calculated using custom rules that you can configure
-
Integrations for synchronizing risks and threats with 3rd party systems

-
Attack Vectors are mapped to each requirement
-
Security standards are linked to each requirement